| 27 ISM
29 Personal Computing Device (PCD) | |
|---|
| 27.29. Personal Computing Device (PCD): | | 1. For people with a personal computing device like a smart phone, tablet, laptop or desktop, sign-in has been improved with the use of a PIN. Traditional sign-in with a password continues for those who share many different computers. | | 2. The unique fingerprint of a personal computing device acts as physical evidence that identifies the person registered to use that device. The PCD fingerprint and a PIN is adequate authentication to replace a password |
| 2. Glossary: | | PCR means "Personal Computing Device" such as a smart phone, tablet, laptop or desktop. | | PIN means "Personal Identifier" such as a 4 digit number. | | BAS means "Bespoke Application Service" providing private online business services. | | PII means "Personally Identifiable Information" that is owned by a living person and with consent may be loaned to a company for a defined purpose. |
| 3. How it works: | | 1. A person with a PCR will self-register their own information and be assigned a unique PIN and password. | | 2. A person will tap in their PIN to sign-in. | | 3. When the person signs in they will remain signed in until they close their browser - this could be months. Sign-off has been eliminated - just close the browser. | | 4. When a person forgets their PIN, they may sign-in with their password. | | 5. When a person gets a different PCD, they may register the device with their password. | | 6. When a person forgets their password, they will self-register and be assigned a different unique PIN and password. After adequate verification, the persons old account and new account will be merged with no loss of data. |
| 4. Self-Registration: | | 1. A person will click to open the self-registration web page as a form. | | 2. A person will enter as much personal information that is required to identify them. | | 3. When the person saves the form, then they are show their unique welcome page with their assgined PIN and password. | | 4. From their welcome page, a person has the right to change their personal information, to download their personal information and to delete their personal information. | | 5. When a person has deleted their personal information, their account is de-activated and cannot be used again. | | 6. No other person can see a persons PIN and a persons PIN cannot be reused by any other person using any other PCD. |
| 5. Sign In: | | 1. A person with a PIN will click on the "sign-in" page and be shown an access pad of 12 buttons. | | 2. A person will tap in their PIN number and click the hash symbol when they have finished. | | 3. If the wrong button is pressed, click the star symbol and restart. | | 4. When the PIN has been entered, the persons unique welcome page is shown - the person has the right to view their PIN and password. | | AS AN ALTERNATIVE: | | 1. A person with a PIN will click on the "password" page and be shown a sign in form. | | 2. A person will enter their name, email, password and select that they accept the terms of use. | | 3. A person is permitted three attempts before any further data entry is simply ignored as criminal behaviour - no error messages are shown. | | 4. When the password has been entered, the persons unique welcome page is shown - the person has the right to view their PIN and password. |
| Example: | 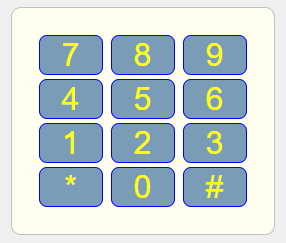 |
| 6. Benefits: | | 1. Where a person uses their smart phone to access their BAS, they can sign-in once and stay signed in until they close their browser. | | 2. Signed in sessions are no longer automatically terminated at midnight. | | 3. A person can view and change their Personally Identifiable Information (PII) at any time. | | 4. The assigned PIN can be used to sign-in using a PCD that has been registered. When another person knows a persons PIN, it is not an issue because the PIN can only be used with the registered PCD. | | 5. The assigned password can be used to sign-in to register any number of new computing devices. | | 6. When a person forgets their PIN is is perfectly reasonable to send the PIN to them by phone or email because the PIN can only be used by the registered device. |
| 7. Fingerprint: | | 1. Every personal computing device has a fingerprint that acts as an additional authentication factor. | | 2. The fingerprint includes: | | (1). Hardware identifier. | | (2). Software identifier. | | (3). Network identifier. | | 3. The network identifier applies to computers with a large screen width, but not to smart phones. | | 4. Behaviour evidence is used for authentication to include: | | (1). Normal business hours of the day, such as 07:00 to 19:00 or 06:00 to 22:00. | | (2). Normal business days of the week, such as Mon-to-Fri or Mon-to-Sat or Mon-to-Sun. | | (3). Night shift working. | | (4). Public holiday working. |
| 8. Management Governance: | | 1. The traditional password is adequate where a person does not use a personal computing device. | | 2. The Bespoke Application Service has a button to popup a simple calculator that can be used for simple arithmetic. | | 3. A manager may be assigned a formula that is used with the calculator to sign in. It has been shown that a secure formula such as "208+428*8366-495/13=" is easier to remember than a secure password. | | 4. The formula is also safe from being "remembered" by the browser and any keylogging malware. |
| Example: | 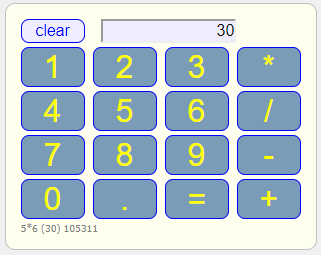 |
| Document Control | | Document Title: ISM Personal Computing Device. | | Document Key Words: ISM, policy, process, procedure, business rules. | | Document Description: ISM PCD Personal Computing Device. | | Document Privacy: Public shared for the benefit of humanity. | | Document Reference: 162729. | | Document Edition: 1.2. | | Document Released: 22 Aug 2017. |
|
|